Since March 2025, a sharp rise in phishing attacks has been observed by KnowBe4 Threat Labs, with hackers exploiting Google’s AppSheet platform to impersonate Meta. This campaign uses advanced tactics such as polymorphic identifiers, man-in-the-middle proxies, and two-factor authentication (2FA) bypass techniques to gain real-time access to social media accounts.
The most significant spike in activity was recorded on 20 April 2025, when 10.88 percent of all phishing emails detected by KnowBe4 Defend globally originated from AppSheet. Of these, 98.23 percent impersonated Meta, while 1.77 percent impersonated PayPal.
Attack Methodology and Exploitation of AppSheet
Hackers are abusing AppSheet, a legitimate Google-owned platform that enables no-code app development and workflow automation. The phishing emails originate from noreply@appsheet.com, a valid sender address, allowing them to bypass domain-based authentication protocols such as SPF, DKIM and DMARC. This legitimate origin helps the emails evade detection by Microsoft 365 and other secure email gateways that rely on sender reputation and domain authentication checks.
The emails impersonate Facebook’s support team and use forged branding to appear genuine. They claim the recipient’s account is at risk of deletion due to a violation, and pressure the user to take action within 24 hours. Subject lines such as “Violating intellectual property rights has caused your account to be deleted” are crafted to induce fear and urgency, compelling users to engage.
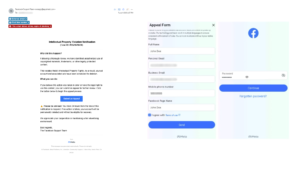
A notable feature of this campaign is the use of polymorphic identifiers, presented as Case IDs in the email body. These unique identifiers ensure that each email is slightly different, making it harder for detection systems to flag them based on static indicators such as content hashes or known malicious URLs. This also complicates the response and remediation efforts for IT teams, who cannot rely on a common identifier for mass blocking or filtering.
Credential and 2FA Harvesting via Proxy-based Infrastructure
When users click on the malicious “Submit an Appeal” link in the email, they are redirected to a fake Meta-branded site hosted on Vercel, a legitimate web hosting platform. The phishing page mimics Facebook’s interface, increasing its credibility. It falsely informs the user that their account is at risk and offers a one-time appeal process.
This phishing site captures credentials and 2FA codes. It prompts users to enter their information twice by claiming the first attempt was incorrect. This tactic increases the chance of capturing accurate data and introduces confusion, reducing the user’s ability to detect the fraud. The site also operates as a real-time man-in-the-middle proxy. When credentials and 2FA codes are entered, they are immediately forwarded to the real Facebook login page. This allows hackers to obtain a valid session token, effectively bypassing two-factor authentication and gaining direct access to the victim’s account.
The Trend of Abusing Legitimate Services to Evade Detection
The use of trusted platforms like AppSheet reflects a broader trend observed by KnowBe4 Threat Labs, where hackers leverage legitimate services to bypass security measures. Similar abuse has been seen with Microsoft, Google, QuickBooks and Telegram. These campaigns often combine impersonation, proxy-based credential harvesting, and social engineering to evade detection and exploit user trust.
Traditional email defences are often ineffective against such tactics. Many organisations are now adopting Integrated Cloud Email Security (ICES) solutions like KnowBe4 Defend, which use artificial intelligence to detect and neutralise sophisticated phishing threats. Furthermore, real-time training based on actual phishing emails, delivered through platforms like KnowBe4 PhishER, is essential for educating users about the latest attack techniques.
This campaign is a clear example of how hackers are adapting to exploit trusted platforms and sophisticated attack chains. It highlights the need for organisations to go beyond basic security controls and adopt advanced defences and continuous user education to remain protected.